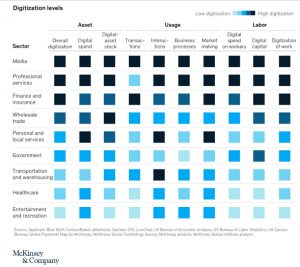
Two consistent and related themes in enterprise technology have emerged in recent years, both involving rapid and dramatic change. One is the rise of the digital enterprise across sectors and internationally. The second is the need for IT to react quickly and develop innovations aggressively to meet the enterprise’s digital aspirations. Exhibit 1 presents a “digitization index”—the results of research on the progress of enterprise digitization within companies, encompassing sectors, assets, and operations.
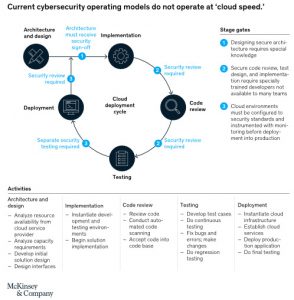
As IT organizations seek to digitize, however, many face significant cybersecurity challenges. At company after company, fundamental tensions arise between the business’s need to digitize and the cybersecurity team’s responsibility to protect the organization, its employees, and its customers within existing cyber operating models and practices.
If cybersecurity teams are to avoid becoming barriers to digitization and instead become its enablers, they must transform their capabilities along three dimensions. They must improve risk management, applying quantitative risk analytics. They must build cybersecurity directly into businesses’ value chains. And they must support the next generation of enterprise-technology platforms, which include innovations like agile development, robotics, and cloud-based operating models.
Cybersecurity’s role in digitization
Every aspect of the digital enterprise has important cybersecurity implications. Here are just a few examples. As companies seek to create more digital customer experiences, they need to determine how to align their teams that manage fraud prevention, security, and product development so they can design controls, such as authentication, and create experiences that are both convenient and secure. As companies adopt massive data analytics, they must determine how to identify risks created by data sets that integrate many types of incredibly sensitive customer information. They must also incorporate security controls into analytics solutions that may not use a formal software-development methodology. As companies apply robotic process automation (RPA), they must manage bot credentials effectively and make sure that “boundary cases”—cases with unexpected or unusual factors, or inputs that are outside normal limits—do not introduce security risks.
About the author(s)
James Kaplan is a partner in McKinsey’s New York office, Wolf Richter is a partner in the Berlin office, and David Ware is an associate partner in the Washington, DC, office.
More: www.mckinsey.com